Critical PrintNightmare Vulnerability Patches
by Vertek Labs
Summary:
Window’s Print Spooler is run by default on all supported Windows operating system versions as it is a legitimate application that manages the printing process on Windows hosts. The flaw in this service allows any low privilege, authenticated user on a network to access the Print Spooler service on an endpoint and use a remote code execution exploit or local privilege escalation to gain SYSTEM privileges.
- On 6/8/2021, a patch was released by Microsoft to mitigate CVE-2021-1675 which is a vulnerability that utilizes the Window’s Print Spooler service as its attack vector to elevate privileges. This vulnerability was initially classified as being low in severity.
- On 6/21/21, Microsoft increased the severity of this vulnerability after third party researchers discovered that this vulnerability can be further exploited to allow remote code execution even after the patch has been installed. Microsoft has since treated this vulnerability as separate from CVE-2021-1675. This newly discovered vulnerability is known as Print Nightmare or CVE-2021-34527.
- On 7/7/2021, Microsoft released an emergency out of band patch to partially remediate CVE-2021-34527, which addresses the remote code execution of the exploit. Although it can still technically be exploited locally to gain SYSTEM privileges.
Vertek’s Response:
Due to the risk of privilege escalation, Vertek recommends installing both of Microsoft’s patches that were released.
- CVE-2021-1675 Patch Information:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1675
- CVE-2021-34527 Patch Information:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527
Important Note about the CVE-2021-34527 Patch: This patch doesn’t address all aspects of the vulnerability, but it does address remote code execution. Even with this patch installed, Print Nightmare can still be exploited locally and then used to gain SYSTEM privileges. There are also several operating systems that do not have a patch yet: Windows 10 version 1607, Windows Server 2016, and Windows Server 2012.
Mitigation:
- If a patch cannot be applied, Microsoft has recommended disabling the Print Spooler service on any Windows systems that is not running print services and to disable inbound remote printing through Group Policy to block inbound remote printing operations if possible.
Steps to determine if the Print Spooler is running on a system as well as steps to disable service and Group Policy:
Source: Microsoft Corporation
- For servers that do require the Print Spooler service to be enabled, such as a print server and that cannot be patched, Truesec has released an ACL workaround that can be used to lock down the service. This ACL rule utilizes a deny rule that prevents the system account from modifying contents in the print driver directory. The ACL can be found here: https://blog.truesec.com/2021/06/30/fix-for-printnightmare-cve-2021-1675-exploit-to-keep-your-print-servers-running-while-a-patch-is-not-available/
Detection:
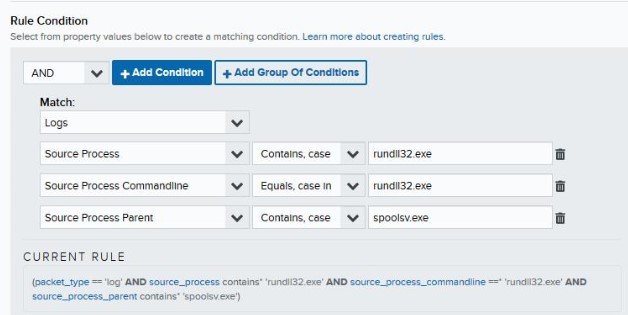
- Vertek’s Threat Intelligence Team has created custom alarm rules to alert on source processes associated with PrintNightmare.
Affected Versions:
- All supported Windows Operating System Versions.
References:
https://threatpost.com/cisa-mitigation-printnightmare-bug/167515/
Recommended Posts
The “Left of Boom”
April 16, 2024
Detecting Anomalous O365 Logins and Evasion Techniques
February 23, 2024