Follina: Microsoft Office Zero Day Vulnerability
by Vertek Labs
On 5/27/22 security research team, Nao_sec identified a malicious Word document in the wild, that appeared to be leveraging the “MS-MSDT” (Microsoft Support Diagnostic Tool) protocol to execute Powershell code. This was done through an external reference in the XML of the Word doc to a malicious HTML file hosted by the threat actor. The malicious HTML file then uses JavaScript to rewrite the URL to call the Microsoft Support Diagnostic Tool via the MS-MSDT protocol and run arbitrary Powershell commands. The exploit does not require the user to have local administrative privileges and can be exploited simply by viewing the file in preview mode. This was suspected at the time to be a 0-day exploit, which was later confirmed by Microsoft and given CVE-2022-30190. This vulnerability was dubbed Follina due to a reference in the observed sample to the area code 0438, which is Follina, Italy.
Vertek’s Response & Mitigation:
There is currently no patch available for this vulnerability. However, several workarounds have been published by CISA and Microsoft while we wait for a patch to be released. Given the severity of this vulnerability if exploited, Vertek would recommend evaluating the following mitigations to see if they can be applied in your environment.
Mitigation via MS Defender’s Attack Surface Reduction (ASR) rules: MS Defender has created a rule named “Office app launching child processes”. Enabling this will stop Office apps from creating child processes which will mitigate a malicious document from being able to run arbitrary commands using MS-MSDT. More information regarding this rule can be found here.
Disabling MSDT URL Protocol: To prevent a malicious file using JavaScript to create a URL that calls to the Microsoft Support Diagnostic Tool, Microsoft has recommended disabling troubleshooters from being launched as links. To disable this, you must complete the following procedure:
Detection:
Vertek’s Threat Intelligence team has created custom USM Anywhere alarm rules to alert on process creations made by the Microsoft Support Diagnostic Tool.
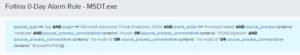
The following rules look for process creations in Microsoft ATP and AlienVault Agent event logs using the source process msdt.exe.
The following rules looks for process creations in Microsoft ATP events made by the parent process sdiagnhost.exe and the child processes, conhost.exe, cmd.exe, or PowerShell
In addition to the alarm rules, AT&T Cyber Security has published an OTX pulse containing a list of IOCs identified after successful exploitation of this vulnerability. The full list of IOCs can be found here.
Affected Versions:
All supported Office applications.
References:
https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
https://www.huntress.com/blog/microsoft-office-remote-code-execution-follina-msdt-bug
https://blog.sekoia.io/msdt-abused-to-achieve-rce-on-microsoft-office/
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-30190
Recommended Posts
The “Left of Boom”
April 16, 2024
Detecting Anomalous O365 Logins and Evasion Techniques
February 23, 2024