Boom, and just like that you are compromised. The “Left of Boom” is the timeframe beforehand, the preventative approach. While much of the industry attention has been on the ability to react quickly and contain intrusions, or “Right of Boom,” it is the prioritization of detecting and responding to a threat before it compromises a system where a truly comprehensive and effective approach lies. Detecting attacks early can make a difference between facing an......
Read More
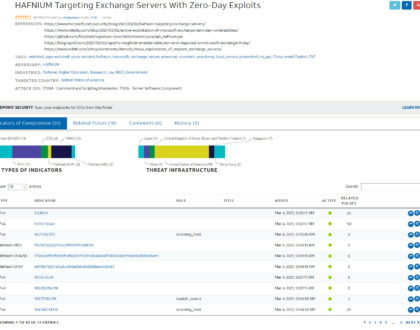
HAFNIUM: Exchange Zero Days Actively Exploited by APT Group
Summary: On 3/2/21, security researchers at Volexity released a blog with their findings following their discovery of four new...
Read MoreSonicWall Product Security Notice
Summary: Last Friday (1/22/21), SonicWall released a statement via their blog that they had been subject to a highly...
Read MoreSolarWinds Breach – SUNBURST Trojan – IOCs
Summary: As of 12/15/20, there have been several high-profile breaches in the media, recently from the U.S Treasury and...
Read MoreUS CERT AA20-302A Alert – Healthcare Cyber-Crime Threat Indicators – OTX Pulse Info
Federal agencies have issued an unprecedented warning against “an increased and imminent cybercrime threat to U.S. hospitals and healthcare...
Read MoreManaged Threat Intelligence: Managed SIEM & SOCaaS Powered by Vertek in 90 seconds
Quickly learn why your organization needs MTI powered by Vertek, and how it will protect you and your customers!...
Read MoreSubscribe to Vertek’s Public OTX Feed
Vertek’s OTX Public and Private Pulses provide a summary of the threat, some information regarding the software targeted, and...
Read MoreLatest Locky Variant Encrypts with Ykcol Extension – IoCs and OTX
As you can see, our labs team is still seeing Locky is being distributed in a lot of malspam...
Read MoreWebsite Ransomware Trending Now
Vertek’s security operations team has noticed website ransomware is starting to pick up steam with recent variants of AwesomeWare,...
Read MoreLocky Now Pushing .Lukitus Variant – IoCs and OTX
Locky is being distributed at mass scale via phishing and spam email attacks by two major botnets; Necurs and...
Read More