Kaseya VSA Attack Delivers REvil Ransomware
Summary: On 07/02/2021, Kaseya disclosed an ongoing attack exploiting on-premise Kaseya VSA servers, along with an advisory to their customers to immediately shut down VSA servers until further notice. Current reports speculate that this is either a supply chain attack or zero-day vulnerability targeting Kaseya VSA Customers for the purposes of deploying REvil ransomware downstream....
Summary:
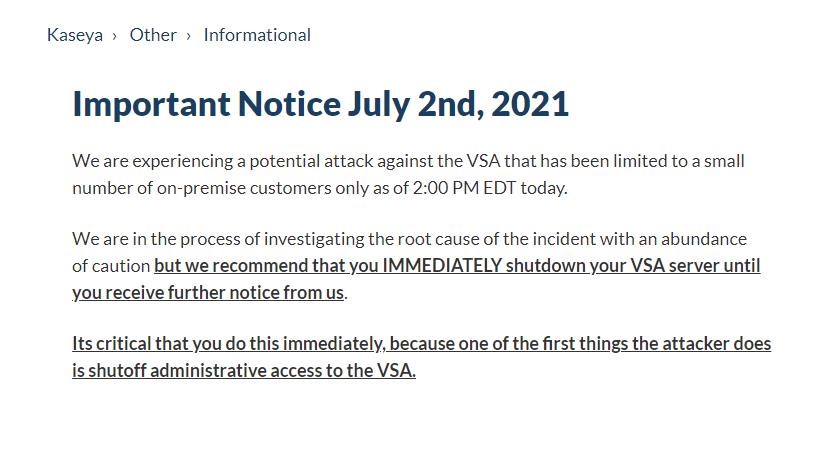
On 07/02/2021, Kaseya disclosed an ongoing attack exploiting on-premise Kaseya VSA servers, along with an advisory to their customers to immediately shut down VSA servers until further notice.
Current reports speculate that this is either a supply chain attack or zero-day vulnerability targeting Kaseya VSA Customers for the purposes of deploying REvil ransomware downstream.
Kaseya VSA is a cloud-based platform that allows organizations to perform remote patching and endpoint management. The inherently elevated privileges leveraged by the Kaseya agent allowed for expedient lateral movement to managed environments. At least 200 companies are reportedly affected by the ransomware thus far.
Kaseya took swift action to protect their customers including an advisory to shutdown VSA Servers until further notice and they shut down SaaS Servers as a precaution. Following established incident response planning, Kaseya mobilized their response team in conjunction with industry forensic experts and federal law enforcement including the FBI and CISA. Refer to the following Kaseya Helpdesk Advisory for the most up to date information as the situation unfolds: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
Vertek’s response:
Due to the critical nature of this attack and the severity of its success, Vertek sent out an alert to our clients informing of Kaseya’s advisory to shut down any VSA servers in their environment until further notice from Kaseya.
Neither Vertek, nor AlienVault USM products utilize any Kaseya services or products internally.
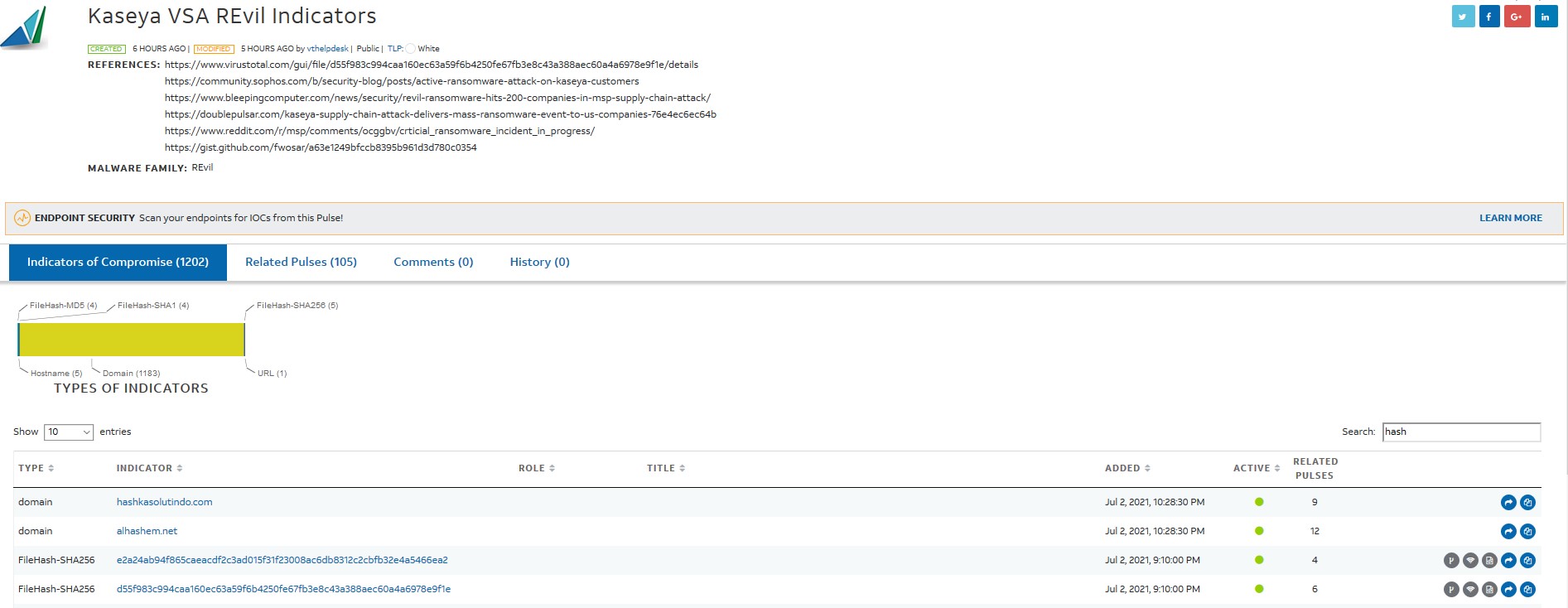
Vertek is invested in providing the latest indicators for this ongoing attack. This can be found in our public OTX pulse: https://otx.alienvault.com/pulse/60df80a7a665c1dd6baf7753/, which will be updated as we receive new indicators of compromise. This pulse is TLP white and anyone can subscribe to it.
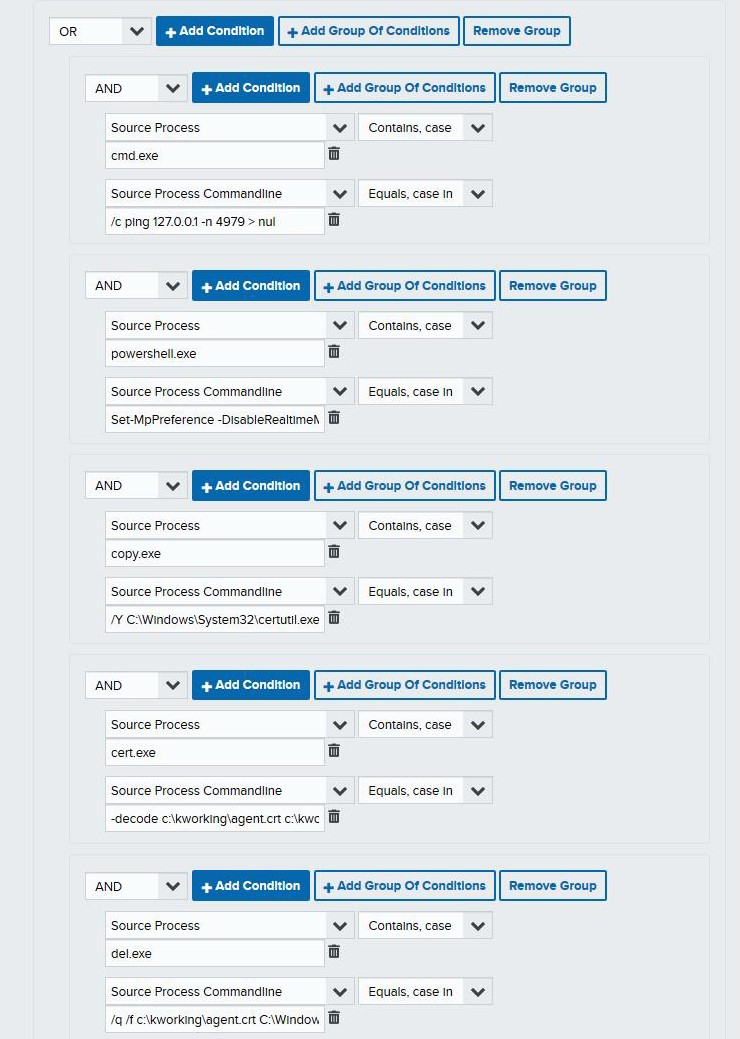
Vertek’s Threat Intelligence Team has created custom alarm rules to detect a cmd.exe source process with the given arguments from the malicious command that executes REvil ransomware:
Affected Version: (Update 7/12/2021)
Following an investigation by Kasyea, they have identified multiple 0-day vulnerabilities affecting both the on-prem VSA software as well as Kaseya’s SAAS platform.
The vulnerabilities are as follows:
- Credential Leak and Business Logic Flaw: CVE-2021-30116
- Cross-Site-Scripting Vulnerability: CVE-2021-30119
- 2FA Bypass: CVE-2021-30120
Patching:
As of 7/11/21 Kaseya has now released patched 9.5.7a, which aims to address the 0-day vulnerabilities previously mentioned as well as other general security improvements.
For on-prem customers, Kaseya has released a guide on what steps to take before bringing the VSA server back online and installing the 9.5.7a patch, as well as a best practice and hardening guide.
For SAAS customers, Kaseya has released a startup guide and best practices guide as well.
Guides for both deployments can be found here, along with additional information regarding the disclosed CVEs.
References / Resources:
https://helpdesk.kaseya.com/hc/en-gb/articles/4403785889041
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
https://us-cert.cisa.gov/ncas/current-activity/2021/07/02/kaseya-vsa-supply-chain-ransomware-attack
https://www.msspalert.com/cybersecurity-breaches-and-attacks/kaseya-rmm-cyberattack-warning/
https://www.reddit.com/r/msp/comments/ocggbv/crticial_ransomware_incident_in_progress/