Citrix ADC/NetScaler RCE CVE-2019-19781
by Vertek Labs
Summary:
On December 17th Citrix published a security bulletin for a recently discovered critical vulnerability in their Citrix ADC and Gateway (formerly known as NetScaler ADC, and NetScaler Gateway) products. The vulnerability, CVE-2019-19781, if exploited would result in an unauthenticated attacker being able to perform arbitrary code execution.
At this time there is no patch available from Citrix however they have published mitigation steps which are outlined here. Over the weekend POC code for this vulnerability was released and is now available to the public, which makes patching this vulnerability more critical than ever.
Affected Versions:
- Citrix ADC and Citrix Gateway version 13.0 all supported builds
- Citrix ADC and NetScaler Gateway version 12.1 all supported builds
- Citrix ADC and NetScaler Gateway version 12.0 all supported builds
- Citrix ADC and NetScaler Gateway version 11.1 all supported builds
- Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
Technical Details:
There are a couple core pieces to this vulnerability; directory traversal and remote code execution. First, a directory traversal flaw in the NetScaler Packet Processing Engine allows a remote attacker to directly access Perl scripts within the /vpns/ directory. Among these Perl scripts is one that takes a request header and crafts a file path without sanitization, allowing the remote attacker to append files to the victim ADC/NetScaler in XML format.
Once the file has been uploaded via the first request, the attacker then sends a second request to execute the previously uploaded file, resulting in a remote code execution attack.
Indicators:
- Review running processes running as user “nobody” – Since the web server runs as the user “nobody”, you can search for running processes owned by “nobody” by running “ps auxd | grep nobody” from the command line of the Citrix host. Initial reports show that very few things outside of /bin/httpd run as user “nobody” and any child processes of httpd should be considered suspicious.
- Review system log files (/usr/bin/bash, httpaccess.log, httperror.log, etc.) for suspicious POST requests, utilizing directory traversal.
- Review for suspicious files under /var/tmp/.
- Review cronjobs that were installed as the user “nobody” (crontab -l -u nobody)
Detection:
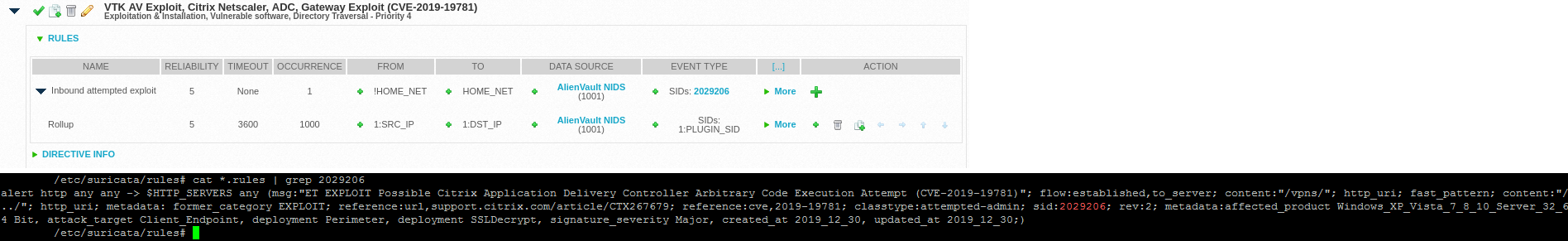
- Suricata has published signatures to detect attempted exploits of this vulnerability. We’ve created a custom directive using that signature to generate alarms when an attempted exploit is seen on the wire.
- Alienvault has published an OTX pulse containing several indicators of compromise that have been observed in the wild and published in industry reports. That OTX pulse can be found here.
- US Cert has published a public tool to test for the vulnerability. For the technically inclined, they can find the tool here, on GitHub.
Prevention:
The best prevention method is published by Citrix and it makes the /vpns/ directory unavailable to remote attackers, preventing access to the vulnerable Perl script(s). There are preliminary reports that the directory traversal requirement is not necessary as the vulnerable Perl scripts can still be directly accessed. However, the mitigation from Citrix will still prevent exploitation in these circumstances as well.
We will update this post with any new information as it becomes available.
Recommended Posts
The “Left of Boom”
April 16, 2024
Detecting Anomalous O365 Logins and Evasion Techniques
February 23, 2024