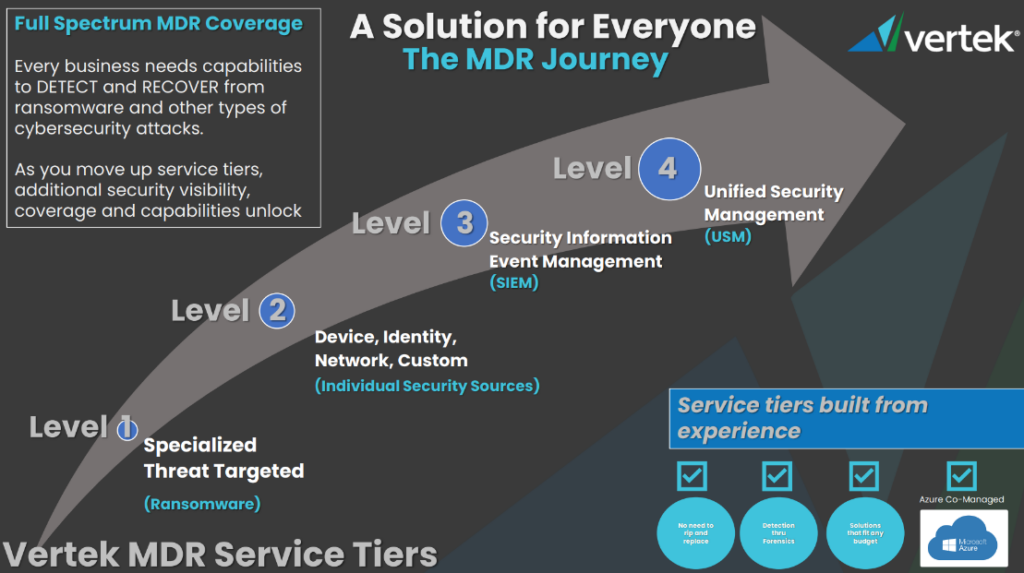
Full Spectrum TDR, EDR, NDR and XDR Coverage
Every business needs capabilities to understand where they are VULNERABLE and capabilities to DETECT and RECOVER from specialized threats such as ransomware and other types of cybersecurity attacks.
As you move up service tiers, additional security visibility, coverage and capabilities unlock
Security Platform Partners:
All MDR services are powered by Vertek's US-Based SOC and include a Vertek proprietary client portal, reports and analytics, DevSecOps integration, playbooks and security orchestration, custom threat intel, 24x7 human-triage and a monthly analyst-led security review.
Security Compliance
Monitoring and reporting, generating evidence artifacts for auditors
Incident Detection
Tuning noisy and non-security related events that cause alarm fatigue
Security Resources
Deploying security orchestration and custom threat detection
Automated Response
Deploying security orchestration and custom threat detection
Demand More From Standard SIEM Analytics
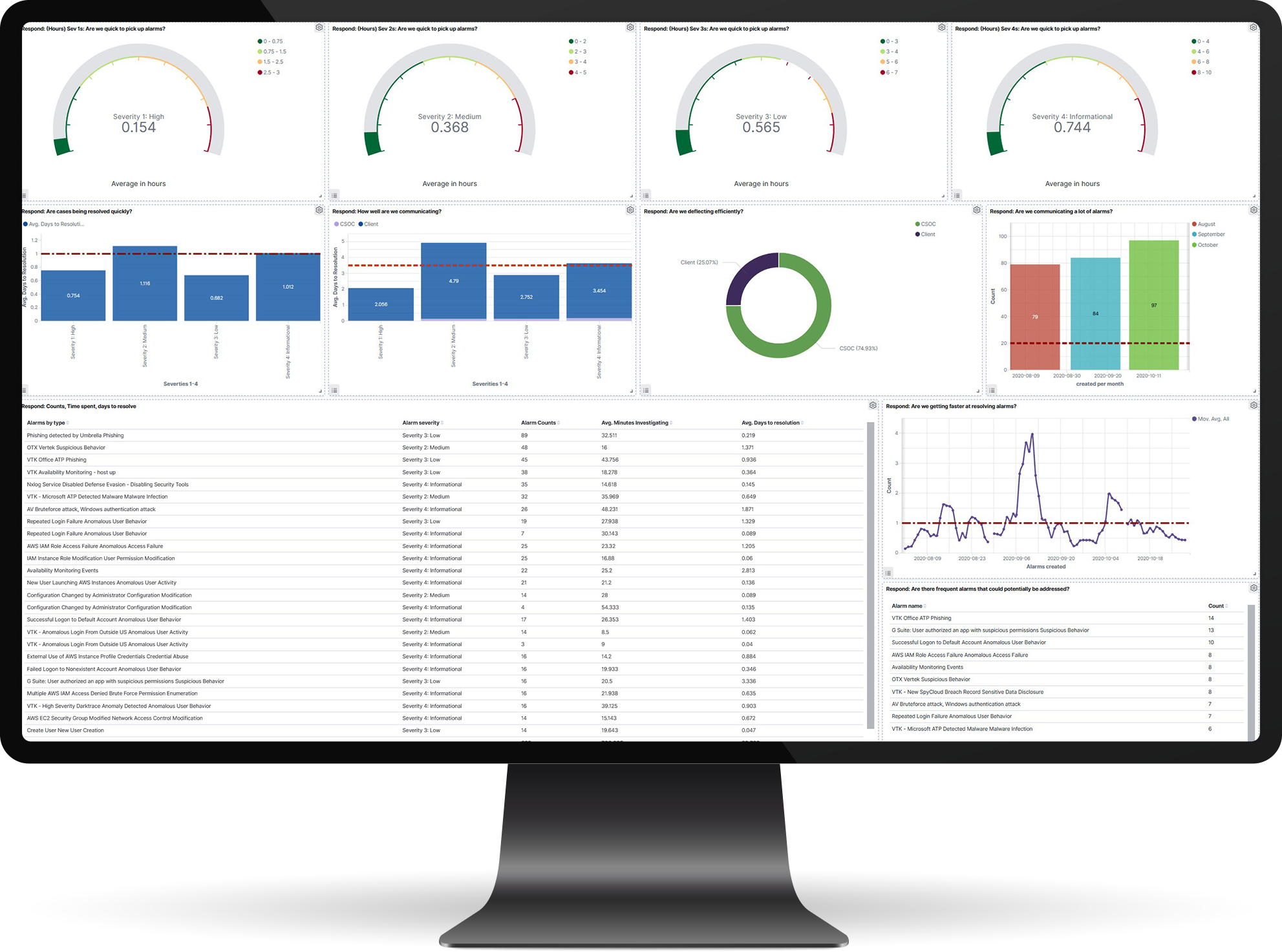
Vertek’s Managed Detection and Response Security Operations team uses proven NIST-based incident response playbooks and superior security engineering resources to help enhance your team’s ability to detect, respond, and remediate threats. We provide actionable response and remediation guidance support you with monthly reporting that tracks alerts, threats, remediation and ticket status.
Top reasons customers choose Vertek:
- I need dedicated security focus, visibility, and analytics
- I need help managing the “flood” of security events
- I need outside security expertise to augment existing staff
- I need assistance meeting regulatory or compliance requirements
- I need to detect non-compliance violations and system or service audit failures
- I need to develop cyber incident and response (IR) capabilities in weeks – not months
What Our Clients and Partners Say About Our High Quality Service

Webinars
Resources
I am text block. Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.





