Managed Unified Security Management
Powered by Vertek
Strategic MSSP Partner
Powered by Vertek
Strategic MSSP Partner

USM Anywhere Is Trusted by 7,000+ Customers
Unlike other SIEM software, Unified Security Management® (USM) combines powerful SIEM and log management capabilities with other essential security tools: asset discovery, vulnerability assessment, intrusion detection, and more. You get centralized security monitoring of your cloud, on-premise, and hybrid environments – all through a single pane of glass.
Vertek realizes no two companies are alike. Through our Managed Detection and Response and Managed Threat Intelligence services we work closely with customers to rapidly detect vulnerabilities, validate real risks and threats, and respond to those threats. We use proven incident response playbooks and superior security engineering resources.
Through our Managed Detection and Response, Managed Threat Intelligence, or Unified Security Management Audit Service, Vertek can optimize, or enhance your USM Anywhere™ deployment with 24x7 monitoring, tuning, management, threat hunting, forensic investigations, reporting or through our dashboards and advanced analytics. We bundle licenses into our Managed Detection and Response, and Managed Threat Intelligence solutions, reducing the time and cost associated with software maintenance, and renewals
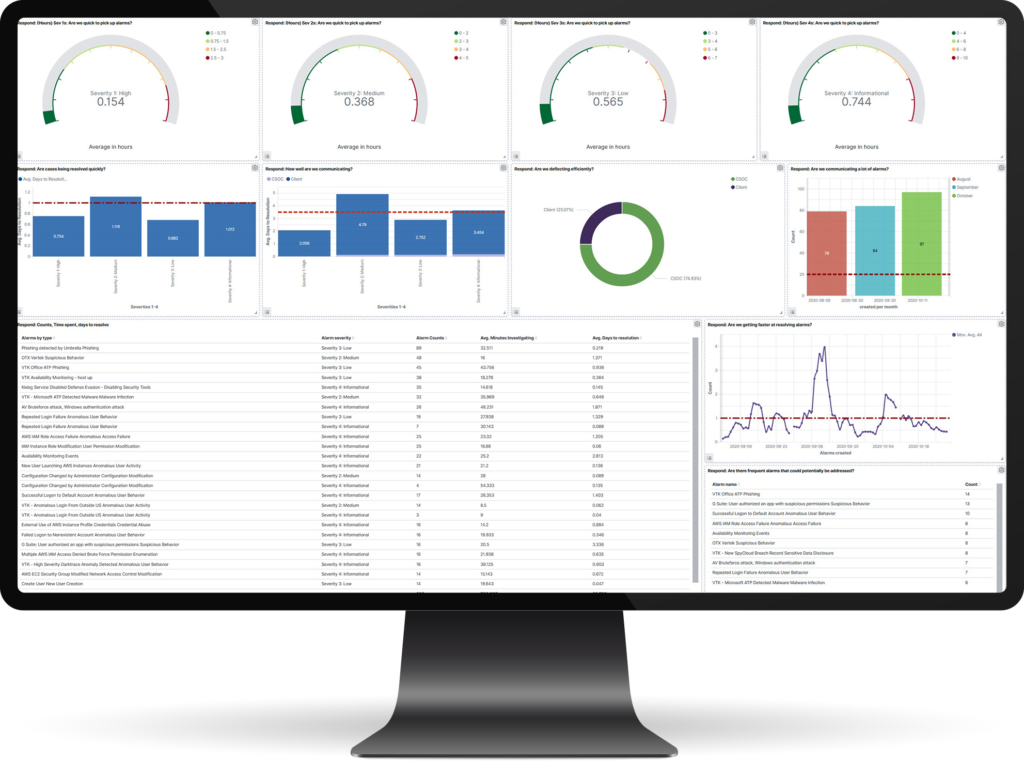
Vertek’s Managed Threat Intelligence Service provides greater visibility into risks and threats, while enhancing your USM Anywhere™ deployment with actionable business intelligence through our dashboards and advanced analytics.
Learn how we do it!
Leveraging host intrusion detection (HIDS), network intrusion detection (NIDS), as well as cloud intrusion detection for public cloud environments including AWS and Microsoft Azure, enables us to detect threats as they emerge in your critical cloud and on-premises infrastructure.
Best of all, Vertek can help you detect threats, respond to attacks, and protect your business quickly, and for a single monthly fee.
| Managed Security Solution Features | MDR | MDR+MTI |
|---|---|---|
| Baseline inventory scanning and asset registration | Included | Included |
| Baseline vulnerability environment scanning | Included | Included |
| Baseline event correlation, tuning and alarm trimming | Included | Included |
| Basic threat dashboard and report creation | Advanced | Advanced |
| SIEM tuning | Continuously | Continuously |
| Vulnerability Scanning | Weekly | Weekly |
| Network IDS and Endpoint Monitoring | Included | Included |
| Security Orchestration, Automation and Response (SOAR) | Included | Included |
| SIEM Alarm Monitoring and Analysis | Included | Included |
| Remediation Guidance | Included | Included |
| Quarterly Service/Relationship Review with TAM | Included | Included |
| Lifecycle and Compliance Report Management | NA | Included |
| Monthly Service/Technical Security Review with Analyst | NA | Monthly |
| Advanced Analytics & Dashboard Reviews | NA | Quarterly |
Discover what you need to know about this unprecedented warning.
15 Reasons why outsourcing will save you time and money
Existing USM Anywhere™ Customers Trust Vertek to Keep Them Secure
Vertek provides proactive Managed Detection and Response, and Managed Threat Intelligence services to USM Anywhere™ customers that can augment your existing security and IT team and accelerate the value and impact of your existing deployment. Our approach to cybersecurity includes a human touch that is supported by industry best practices and a decade of experience providing managed SIEM, SOC, and powerful analytics to clients across dozens of industries.
Our Managed Detection and Response, Managed Threat Intelligence, and USM Anywhere™ Audit services are customized to meet your unique business and security requirements. These services are designed to reduce risk and accelerate the evolution of your cybersecurity program and posture. Embrace the value of high-end security solutions backed by human intelligence and experience. Reach out to us today.
"*" indicates required fields