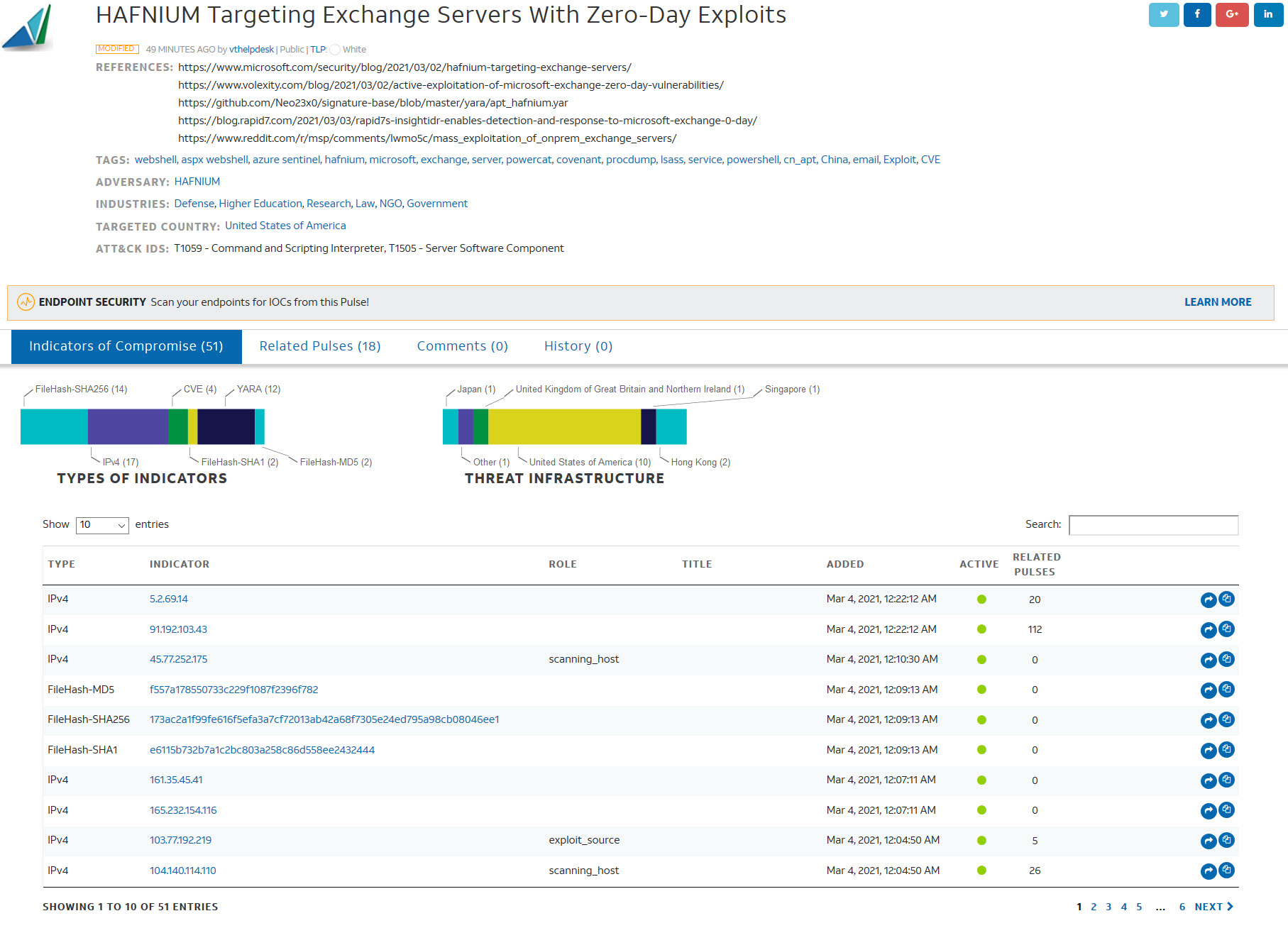
HAFNIUM: Exchange Zero Days Actively Exploited by APT Group
Summary: On 3/2/21, security researchers at Volexity released a blog with their findings following their discovery of four new Microsoft Exchange Server 0-day vulnerabilities. Volexity first detected exploitation in one of their customers back in January 2021. The discovered vulnerabilities are as follows: CVE-2021-26855 A Server-Side Request Forgery (SSRF) vulnerability allows for authentication bypass when...
Summary:
On 3/2/21, security researchers at Volexity released a blog with their findings following their discovery of four new Microsoft Exchange Server 0-day vulnerabilities. Volexity first detected exploitation in one of their customers back in January 2021.
The discovered vulnerabilities are as follows:
- CVE-2021-26855
- A Server-Side Request Forgery (SSRF) vulnerability allows for authentication bypass when sending arbitrary HTTP requests.
- Successful exploitation is dependent on how Exchange is configured, either in a single server configuration or a Database Availability Group (DAG).
- It also requires the attacker to know the target’s email address and the fully qualified domain name (FQDN) of the Exchange server(s).
- In the event of a single server configuration, an attacker would also need to know the domain SID of the target user.
- CVE-2021-26857
- An insecure deserialization vulnerability in the Unified Messaging service allows for code to be run as SYSTEM.
- This vulnerability requires the chaining of an authentication bypass vulnerability or administrator privileges to exploit successfully.
- CVE-2021-26858 & CVE-2021-27065
- Both are post-authentication arbitrary file write vulnerabilities that require the chaining of an authentication bypass vulnerability or administrator privileges to exploit successfully.
Microsoft, who through their own investigation was able to attribute the activity to the Chinese APT group, HAFNIUM.
HAFNIUM has been observed chaining the SSRF vulnerability into the other three vulnerabilities to conduct multiple post-compromise activities, including but not limited to the following:
- Stealing full contents of user’s mailboxes.
- Deploying ASP web shells for persistence.
- Dumping credentials.
- Adding accounts.
- Exfiltrating copies of the Active Directory database (NTDS.DIT).
- Lateral movement across the network.
Affected Versions:
- Microsoft Exchange Server 2013
- Microsoft Exchange Server 2016
- Microsoft Exchange Server 2019
Vertek’s Response:
- Due to the critical nature of these vulnerabilities and the large amount of scanning activity, looking for vulnerable Exchange servers, Vertek recommends patching these vulnerabilities ASAP. Patches for the affected Exchange versions can be found on Microsoft’s website, here.
- If a patch cannot be applied in a timely manner, we recommend restricting port 443 to your public facing Exchange front-end in the interim.
- Optionally, block malicious IPs, which can be found in the Vertek maintained OTX Pulse here. This includes currently known IoCs which we will be keeping updated.
- We also urge you to check for the existence of any installed webshells due to the automated exploitation of this vulnerability. Check these paths for any oddly named .aspx files:
- C:\inetpub\wwwroot\aspnet_client\
- C:\inetpub\wwwroot\aspnet_client\system_web\
- C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\
References:
- https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/
- https://www.volexity.com/blog/2021/03/02/active-exploitation-of-microsoft-exchange-zero-day-vulnerabilities/
- https://twitter.com/GossiTheDog/status/1366894548593573893?s=20
- https://www.tenable.com/blog/cve-2021-26855-cve-2021-26857-cve-2021-26858-cve-2021-27065-four-microsoft-exchange-server-zero-day-vulnerabilities